PKI
This section is going further and demonstrates how a custom Certificate Authority (CA) can be used to securely connect devices to a West Connectivity Connector product.
Configuration
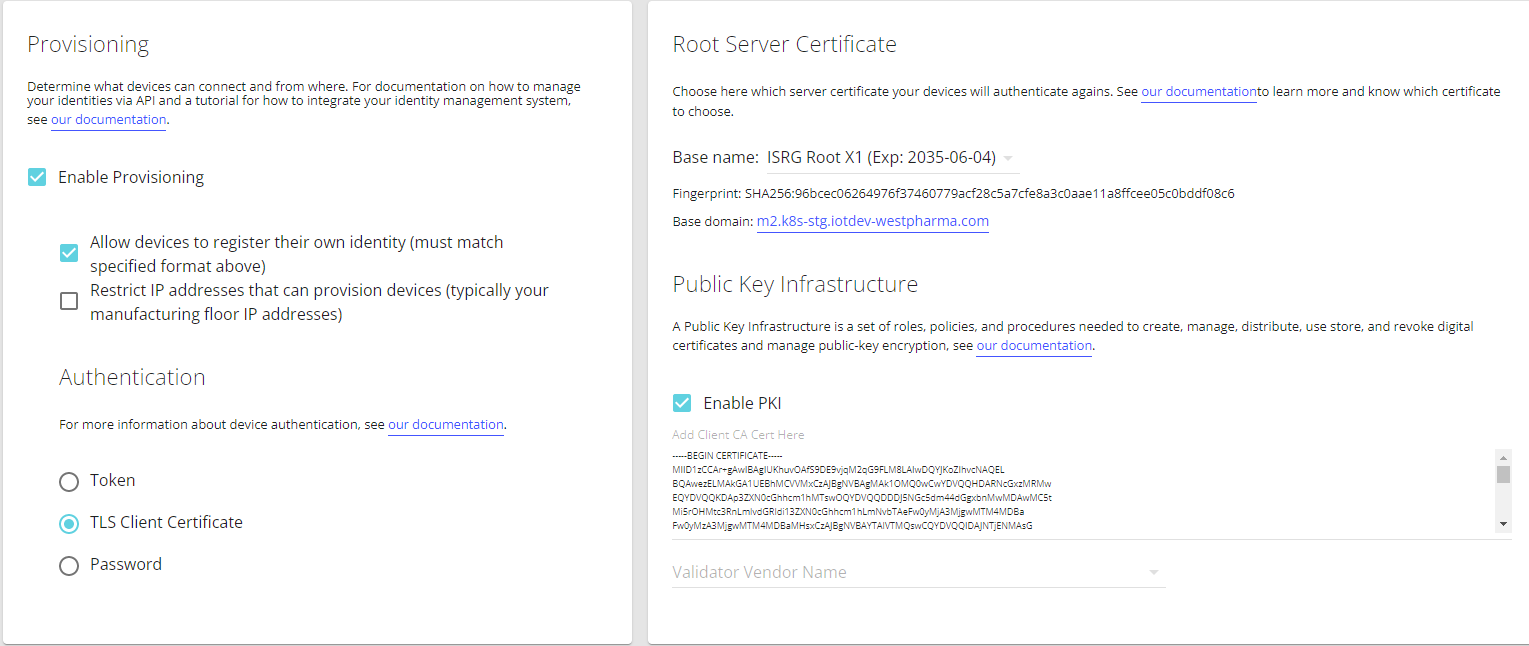
Navigate to the Connector Product page under the Settings tab.
In the Provisioning section, select the TLS Client Certificate authentication method and leave everything else at their defaults.
In the Public Key Infrastructure section, check the box next to Enable PKI. This will reveal a text box titled Add Client CA Cert Here.
That is where you have to paste your Client CA Certificate in PEM format.
Here is an example to create a Client CA:
openssl req -x509 -nodes -days 365 -sha256 -subj /C=US/ST=MN/L=Mpls/O=westpharma/CN=<The-domain-of-connector> -newkey rsa:2048 -keyout <Key-name>-key.pem -out <Cert-name>-cert.pem
Your settings should look like the following (Expect for the optional Vendor Validator options):
Now, click the SAVE button in the upper right corner to commit your changes to your product's settings.
At this point, your West Connectivity Cloud setup is ready.
Connecting Device
In the previous section, we left the Enable Provisioning and Allow devices to register their own identity options selected. Because of that, we don't need to explicitly whitelist a device for provisioning. The device can simply connect to West Connectivity with its client side certificate provided and West Connectivity will automatically save the device's identity (Common Name extracted from the certificate) and certificate for subsequent authentication. On top of that, devices using TLS Client Certificate authentication, do not need to explicitly call the activate endpoint to get provisioned. Instead, they can start sending data on their first connection.
For the --cert option, use the client side certificate (signed by the configured Client CA). For the --key option, use the private key.
Here is an example to generate a client side certificate signed by the configured Client CA:
openssl req -new -nodes -days 365 -sha256 -subj /C=US/ST=MN/L=Mpls/O=westpharma/CN=<Device-name> -newkey rsa:2048 -keyout <Device-name>-key.pem -out <Device-name>.csr
openssl x509 -req -in <Device-name>.csr -CA <Cert-name>-cert.pem -CAkey <Key-name>-key.pem -CAcreateserial -out <Device-name>.pem -days 365
You can use below example to provision a device and publish data to West Connectivity:
curl -v \
-X POST https://<The-domain-of-connector>/api:v1/stack/alias \
--cert ./<Device-name>.pem \
--key ./<Device-name>-key.pem \
-d temperature=50
The above command has now provisioned the device and wrote the value 50 with the alias "temperature". West Connectivity has verified that the provided certificate had been signed by the Client CA Certificate that is configured for this product.
Issuing the same command subsequently, will cause West Connectivity to use the client certificate to identify (by extracting the Common Name) and authenticate the device (by verifying that the client certificate has been issued by the configured Client CA Certificate and by checking whether the provided certificate has been associated with the connecting device in West Connectivity's database).